ISO 27001
If you’ve ever lost sleep worrying about data breaches, cyber attacks, or whether your organization’s sensitive information is truly secure, you’re not alone. In today’s digital landscape, where a single security incident can cost millions and destroy years of hard-earned reputation, businesses across the UAE and globally are asking themselves one critical question: “How do we prove we’re serious about information security?”
That’s exactly where ISO 27001 comes in.
Whether you’re a business owner investigating security standards for the first time, an IT professional looking to advance your career, or a compliance officer tasked with implementing a robust security framework, this guide will walk you through everything you need to know about ISO 27001—without the jargon, without the confusion.
What Is ISO 27001? Understanding the Gold Standard of Information Security
ISO 27001 (formally known as ISO/IEC 27001) is the internationally recognized standard for Information Security Management Systems (ISMS). Think of it as a comprehensive blueprint that helps organizations of any size, in any industry, systematically manage and protect their valuable information assets.
But here’s what makes it different from other security measures: ISO 27001 isn’t just a checklist of technical controls. It’s a complete management system that weaves security into the very fabric of how your organization operates.
The core principle? Risk-based thinking. Instead of applying generic security measures, ISO 27001 requires you to identify your specific risks and implement controls that make sense for your unique situation.
Why ISO 27001 Matters Now More Than Ever
Consider these sobering statistics: According to IBM’s Cost of a Data Breach Report 2024, the average cost of a data breach reached $4.88 million globally. In the Middle East, organizations faced average costs of $8.75 million per breach. These aren’t just numbers—they represent real businesses dealing with regulatory fines, legal costs, customer compensation, and irreparable damage to their reputation.
When you implement ISO 27001, you’re not just protecting data. You’re:
- Building customer trust through demonstrable security commitment
- Meeting regulatory compliance requirements across multiple jurisdictions
- Creating competitive advantage in tenders and contracts
- Reducing the likelihood and impact of security incidents
- Establishing a culture of continuous security improvement
The Business Case: Why Organizations in the UAE Are Pursuing ISO 27001 Certification
Working with businesses across Dubai, Abu Dhabi, and the broader UAE region, I’ve witnessed firsthand the transformation that ISO 27001 brings. Here’s what drives organizations to pursue this certification:
Regulatory Pressure: With regulations like the UAE Data Protection Law and sector-specific requirements from authorities like the Dubai Financial Services Authority (DFSA), compliance isn’t optional—it’s mandatory.
Client Requirements: Major corporations and government entities increasingly require their suppliers and partners to hold ISO 27001 certification. Without it, you’re simply not invited to bid on lucrative contracts.
Insurance Benefits: Many cyber insurance providers offer reduced premiums for ISO 27001-certified organizations, recognizing the reduced risk profile.
Operational Excellence: Beyond compliance, the structured approach improves efficiency, reduces security incidents, and creates clarity around roles and responsibilities.
Understanding the ISO 27001 Framework: Key Components Explained
Let me break down the essential elements of ISO/IEC 27001 in a way that actually makes sense:
The Structure of ISO 27001
| Component | What It Covers | Why It Matters |
|---|---|---|
| Clauses 4-10 | Requirements for establishing, implementing, maintaining, and continually improving the ISMS | These are mandatory requirements your organization must meet for certification |
| Annex A | 93 security controls across 4 themes (Organizational, People, Physical, Technological) | You select which controls apply based on your risk assessment |
| Context of the Organization | Understanding internal/external issues, interested parties, and ISMS scope | Ensures the ISMS is relevant to your actual business situation |
| Leadership | Management commitment, security policy, roles and responsibilities | Without leadership buy-in, your ISMS is just paperwork |
| Risk Assessment & Treatment | Identifying, analyzing, and responding to information security risks | The heart of ISO 27001—everything flows from understanding your risks |
The PDCA Cycle: How ISO 27001 Works in Practice
ISO 27001 follows the Plan-Do-Check-Act methodology, creating a continuous improvement loop:
PLAN → Define ISMS scope, assess risks, select controls
↓
DO → Implement risk treatment plan and controls
↓
CHECK → Monitor, measure, audit, and review ISMS performance
↓
ACT → Take corrective actions, continually improve
↓
(Back to PLAN)This isn’t a “set it and forget it” certification. The standard requires ongoing commitment to security improvement, which is exactly why it remains relevant as threats evolve.
ISO 27001 certification process
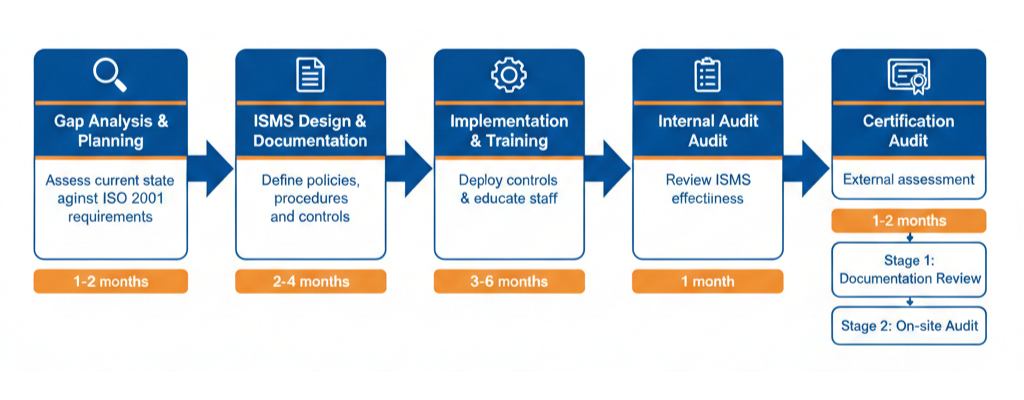
The Certification Journey: What to Expect When Pursuing ISO 27001
Let’s be honest: achieving ISO 27001 certification requires significant effort. But understanding the path makes it manageable. Here’s the typical journey organizations take:
Phase 1: Gap Analysis and Planning (1-2 months)
This is where you are right now—figuring out where you stand. A thorough gap analysis identifies:
- What security controls you already have in place
- Where the gaps exist between your current state and ISO 27001 requirements
- The resources (time, money, people) you’ll need to close those gaps
- Realistic timelines for implementation
Pro tip from experience: Don’t skip this phase. Organizations that rush into implementation without proper planning inevitably waste time and resources fixing avoidable mistakes.
Phase 2: ISMS Design and Documentation (2-4 months)
This phase involves creating the foundation of your ISMS:
- Defining your scope (what information assets and processes are included)
- Conducting comprehensive risk assessments
- Developing policies, procedures, and work instructions
- Creating the Statement of Applicability (SoA) that documents which Annex A controls you’ve implemented
The documentation doesn’t need to be perfect—it needs to be practical. I’ve seen organizations create beautifully written policies that nobody follows because they’re disconnected from actual operations. Your documents should reflect how your business really works.
Phase 3: Implementation and Awareness (3-6 months)
Here’s where theory meets reality. You’ll:
- Deploy selected security controls across your organization
- Train staff on their roles and responsibilities
- Establish monitoring and measurement processes
- Test incident response procedures
- Collect evidence that controls are operating effectively
Common challenge: Getting busy employees to adopt new security practices. The solution? Make security easy, explain the “why” behind requirements, and secure visible leadership support.
Phase 4: Internal Audit (1 month)
Before facing external auditors, you need to audit yourselves. This critical step:
- Identifies non-conformities you can fix before certification audit
- Tests whether your ISMS actually works as documented
- Provides practice for the certification process
- Demonstrates your commitment to continual improvement
Phase 5: Certification Audit (1-2 months)
The certification audit happens in two stages:
Stage 1 (Documentation Review): The auditor reviews your ISMS documentation to ensure it meets ISO 27001 requirements. They’ll identify any major gaps before proceeding to Stage 2.
Stage 2 (Implementation Audit): The auditor visits your organization to verify that your ISMS is actually implemented and operating effectively. They’ll interview staff, observe processes, and examine evidence.
If you pass, congratulations—you’re ISO 27001 certified! The certificate is valid for three years, with annual surveillance audits to ensure you maintain compliance.
The Role of ISO 27001 Consultants in UAE: When to Seek Expert Help
Here’s an uncomfortable truth: while it’s technically possible to pursue ISO 27001 certification without external help, most organizations benefit significantly from working with experienced ISO 27001 consultants in UAE.
What Professional Consultants Bring to the Table
Having guided dozens of organizations through certification, I can tell you that expert consultants provide:
Industry-Specific Knowledge: Understanding how ISO 27001 applies to your specific sector (finance, healthcare, technology, government) saves months of trial and error.
Resource Efficiency: Consultants know exactly what auditors look for, helping you focus efforts where they matter most rather than over-documenting low-risk areas.
Local Regulatory Insight: UAE-based consultants understand regional compliance requirements and how ISO 27001 integrates with local regulations.
Unbiased Perspective: Internal teams sometimes struggle to challenge existing practices. External consultants bring fresh eyes and can ask difficult questions without political complications.
Accelerated Timeline: What might take 18 months internally often takes 8-12 months with experienced consulting support.
Choosing the Right Consulting Partner
Not all consultants are created equal. When evaluating potential partners, consider:
- Proven track record: Ask for client references and examples of successful certifications in your industry
- Qualified auditors on staff: Look for consultants with ISO 27001 Lead Auditor certification
- Practical approach: Avoid consultants who focus solely on documentation without considering your operational reality
- Knowledge transfer: The best consultants teach your team to maintain the ISMS independently, not create dependency
- Local presence: For UAE-based organizations, having consultants who understand the regional business environment is invaluable
ISO 27001 Lead Auditor Certification: Building Internal Expertise
While external consultants jumpstart your certification journey, building internal capability ensures long-term success. This is where ISO 27001 Lead Auditor certification becomes strategic.
What Is ISO 27001 Lead Auditor Training?
This intensive 5-day program teaches individuals how to:
- Plan, conduct, report, and follow up on ISMS audits
- Interpret ISO 27001 requirements in various organizational contexts
- Lead audit teams effectively
- Identify non-conformities and assess their severity
- Apply risk-based thinking to audit processes
Who should pursue this certification?
- Internal auditors responsible for maintaining your ISMS
- IT security professionals seeking career advancement
- Compliance officers managing multiple standards
- Consultants building professional credentials
- Quality managers expanding their expertise
The Business Benefits of In-House Lead Auditors
Organizations with certified lead auditors on staff gain several advantages:
Cost Savings: Conducting internal audits with qualified staff eliminates ongoing external audit costs beyond the mandatory certification audits.
Faster Response: Internal auditors understand your organization intimately and can quickly assess new risks or changes without the ramp-up time external auditors need.
Continuous Improvement: Rather than viewing audits as annual compliance exercises, organizations with internal expertise embed auditing into their continuous improvement culture.
Enhanced Credibility: Having ISO 27001 Lead Auditor certified staff demonstrates serious commitment to information security, strengthening customer confidence.
Common Challenges and How to Overcome Them
Let me share some real-world challenges I’ve seen organizations face—and more importantly, how to address them:
Challenge 1: “We’re too small for ISO 27001”
Reality: ISO 27001 scales to organizations of any size. Small businesses can implement proportionate controls that fit their risk profile. In fact, smaller organizations often achieve certification faster than large enterprises due to less complexity.
Solution: Start with a tightly focused scope covering your most critical information assets. You can always expand later.
Challenge 2: “Our employees see security as IT’s problem”
Reality: Information security is everyone’s responsibility. The human element remains the weakest link in most security incidents.
Solution: ISO 27001 requires documented security awareness training. Make it engaging, relevant to each role, and repeated regularly. When staff understand how security protects their jobs and the organization’s future, engagement improves dramatically.
Challenge 3: “The documentation burden is overwhelming”
Reality: Yes, ISO 27001 requires documentation—but not as much as you fear.
Solution: Create concise, practical documents that people actually use. Leverage templates and existing documentation where possible. Focus on quality over quantity.
Challenge 4: “We can’t afford the investment”
Reality: The cost of NOT having robust information security often exceeds the cost of certification.
Solution: Calculate the potential cost of a data breach for your organization. Include direct costs (incident response, legal fees, fines) and indirect costs (reputation damage, customer loss, business disruption). Suddenly, ISO 27001 looks like excellent insurance.
ISO 27001 vs. Other Security Standards: How They Compare
You might be wondering how ISO 27001 relates to other security frameworks. Here’s a quick comparison:
ISO 27001 vs. SOC 2: ISO 27001 is an international standard suitable for any organization, while SOC 2 is primarily used by US-based service organizations. ISO 27001 tends to be more comprehensive in scope.
ISO 27001 vs. NIST Cybersecurity Framework: NIST provides excellent guidance but isn’t a certifiable standard. Many organizations use both—NIST for framework and ISO 27001 for certification.
ISO 27001 vs. PCI DSS: PCI DSS specifically addresses payment card security and is mandatory for organizations handling card data. ISO 27001 covers broader information security and is voluntary (though often required by contracts). They’re complementary, not alternatives.
ISO 27001 vs. GDPR: GDPR is data protection legislation, not a management system. However, implementing ISO 27001 significantly helps with GDPR compliance, particularly regarding data security requirements.
Maintaining Certification: Life After Certification Day
Achieving certification is a major milestone—but it’s not the finish line. Here’s what happens next:
Year 1-2: Surveillance Audits
Your certification body conducts annual surveillance audits to verify you’re maintaining and improving your ISMS. These are typically shorter and less intensive than the initial certification audit.
Focus areas: Evidence of continual improvement, corrective actions from previous audits, management review outputs, and any significant changes to your organization or ISMS.
Year 3: Recertification Audit
After three years, you undergo a full recertification audit similar to your original Stage 2 audit. This ensures your ISMS remains effective and aligned with current ISO 27001 requirements.
Continuous Improvement Activities
Between audits, your ISMS should be dynamic and responsive:
- Regular risk assessments (at least annually, or when significant changes occur)
- Internal audits covering the entire ISMS scope over a planned period
- Management reviews to evaluate ISMS performance and opportunities for improvement
- Monitoring of security incidents and near-misses
- Updates to controls as threats evolve
- Staff training and awareness programs
The organizations that thrive with ISO 27001 treat it as a valuable management tool, not just a certification to maintain. They use the framework to drive real security improvements that protect their business.
The ROI of ISO 27001: Measuring Success Beyond Certification
Let’s talk numbers. While the investment in ISO 27001 certification varies (typically $30,000-$150,000 depending on organization size and complexity), the return manifests in multiple ways:
Tangible Returns
- Reduced security incidents: Organizations typically see 30-50% reduction in security incidents within the first year
- Lower insurance premiums: Cyber insurance discounts of 10-30% are common
- Increased contract wins: Access to opportunities previously unavailable, often worth millions
- Reduced audit costs: Single certification satisfies multiple client security requirements
Intangible Returns
- Enhanced reputation and competitive positioning
- Improved employee awareness and security culture
- Greater confidence among customers and stakeholders
- Clearer accountability and governance
- Foundation for additional certifications (ISO 22301, ISO 20000, etc.)
Your Next Steps: Making ISO 27001 a Reality
If you’ve read this far, you’re serious about information security. Here’s your action plan:
Immediate Actions (This Week)
- Assess your readiness: Conduct an honest evaluation of your current security posture
- Secure leadership buy-in: Present the business case to key stakeholders
- Define your scope: Identify which parts of your organization will be included
- Budget appropriately: Account for consulting, training, certification, and internal resources
Short-term Actions (This Month)
- Engage ISO 27001 consultants: Research and meet with potential consulting partners
- Identify project team: Assign internal champions who will drive the initiative
- Begin risk assessment: Start identifying your information assets and associated risks
- Plan training: Identify staff who need ISO 27001 awareness or lead auditor certification
Long-term Commitment (Next 6-12 Months)
- Follow your implementation roadmap: Work through each phase systematically
- Build security culture: Make information security part of your organizational DNA
- Monitor progress: Track milestones and adjust plans as needed
- Prepare for certification: Conduct thorough internal audits before the external assessment
Why Choose M2Y Safety Consultancy for Your ISO 27001 Journey
Navigating ISO 27001 certification doesn’t have to be overwhelming. At M2Y Safety Consultancy, we’ve helped organizations across the UAE achieve certification efficiently and effectively, building lasting security capabilities rather than just checking boxes.
Our Approach
We combine deep technical expertise with practical business understanding. Our team includes certified ISO 27001 Lead Auditors with real-world implementation experience across diverse industries—from technology startups to government entities to established financial services firms.
What sets us apart:
- Tailored solutions: We recognize that no two organizations are identical. Your ISMS will reflect your unique business context, risks, and objectives
- Knowledge transfer: We don’t just implement—we teach your team to maintain and improve your ISMS independently
- Efficient timelines: Our proven methodology accelerates certification without cutting corners
- Ongoing support: From gap analysis through certification and beyond, we’re your partners in information security excellence
Our Services Include
ISO 27001 Consulting: End-to-end support from gap analysis through successful certification, including ISMS design, documentation development, implementation support, and audit preparation.
ISO 27001 Lead Auditor Training: Comprehensive 5-day programs that equip your team with the skills to conduct professional ISMS audits, delivered by experienced auditor trainers.
Risk Assessment Workshops: Facilitated sessions that help you identify and prioritize your information security risks using proven methodologies.
Internal Audit Services: Professional internal audits conducted by our certified lead auditors, providing objective assessment of your ISMS effectiveness.
ISMS Maintenance: Ongoing support to help you maintain certification and continually improve your security posture.
Final Thoughts: Information Security Is a Journey, Not a Destination
ISO 27001 certification represents a significant achievement—proof that your organization takes information security seriously and has implemented a robust management system. But the real value lies not in the certificate on your wall, but in the security culture you build, the risks you mitigate, and the trust you earn from customers and stakeholders.
In an era where cyber threats evolve daily and data breaches make headlines weekly, ISO 27001 provides the structured, risk-based approach organizations need to protect what matters most. It’s an investment in your business’s resilience, reputation, and future.
The question isn’t whether you can afford to pursue ISO 27001 certification. The question is whether you can afford not to.
Ready to begin your ISO 27001 journey? Contact M2Y Safety Consultancy today for a complimentary consultation. Let’s discuss your specific security challenges and create a roadmap to certification that works for your organization.
About M2Y Safety Consultancy: We’re a leading provider of ISO certification consulting and training services in the UAE, helping organizations across Dubai, Abu Dhabi, and the region achieve excellence in information security, quality management, and business continuity. Our team of certified experts brings practical experience and professional guidance to every engagement, ensuring you achieve certification efficiently while building lasting capability.
Contact us today to schedule your free ISO 27001 gap assessment and take the first step toward world-class information security.















































